ADCS: Setting up domain-joined device certificate auto-enrolment for all, or specific, devices.
Automatically deploy a certificate template from Active Directory Certificate Services (ADCS) to Active Directory domain-joined devices, referred to as "auto-enrolment".

This page has all the required information in order to automatically deploy a certificate template from Active Directory Certificate Services (ADCS) to Active Directory domain-joined devices, referred to as "auto-enrolment".
Automatically enrolled certificates are also automatically renewed provided the machine is able to communicate with ADCS at the time of renewal.
Some common reasons you might want to do this are securing RDP sessions across your environment with SSL/TLS certificates, deploying device certificates for SCCM enrolment, or for integration with a third-party vendor's system.
Required Pre-requisites
- You already have a server configured and with the ADCS Active Directory-integrated issuing certificate authority role installed (and set up).
- You have already created (or identified an existing) suitable AD security group which contains the devices computer objects which are to be enrolled. In the example, we will deploy to the "All Computers" group, but you can be as granualar as you want with this.
- You have created a certificate template in ADCS with the relevant applicable properties that meets the requirements of the certificate you want to deploy. Typically that would be based on information from the vendor and/or by cloning an existing ADCS certificate template.
- Do this within the Certificate Templates MMC snap-in, worth noting that this is separate from the Certificate Authority snap-in.
Steps to auto-enroll
Firstly, create an ADCS auto-enrollment enabled GPO
Firstly you'll need to create a GPO which enables automatic certificate enrollment on the domain. This doesn't deploy the certificates directly, rather it enables auto-enrollment of AD published certificate templates.
Create a GPO, in our example it'll be GPO_COM_ADCS_CertEnroll, and disable the User Policy side of the GPO. This is a computer policy object.
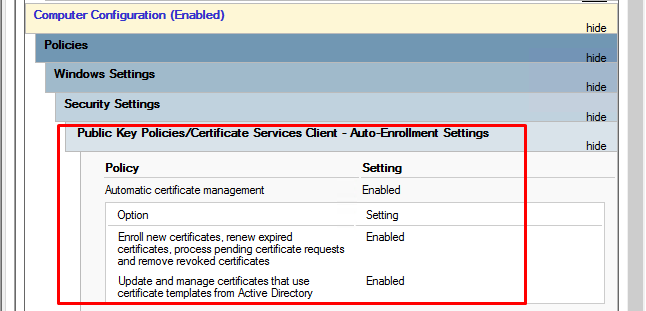
The GPO options you require are:
Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies > Certificate Service Client - Auto-Enrollment Settings. Then select Automatic certificate management (Enable this), with the options Enroll new certificates, renew expired certificates, process pending certificate requests and remove revoked certificates (Enable this), and Update and manage certificates that use certificate templates from Active Directory (Enable this too)
As with all GPOs, firstly attach this GPO to a test OU to ensure nothing unexpected occurs within your org's GPO stack, before rolling it out across the organization. Ideally, once testing is successful, this GPO needs attaching at the root of the domain. Note that you won't be able to test this GPO until you have published at least one certificate template to AD.
Now we've prepared our AD environment to auto-deploy published certificate templates, we'll get ready to publish our certificates.
Open the “Certificate Templates” MMC snap-in (this is separate from the Certification Authority snap-in) on your issuing CA server, and locate the certificate template that you wish to auto-enroll.
Firstly, we need to check the Security settings have been set correctly. With an Active Directory Certificate Services published certificate template, the security settings dictate which devices will automatically grab a certificate.
On the “Security tab” ensure that the chosen AD security group containing all devices to automatically enroll has the permissions “Auto-enroll” and “Read”.
For example, if all domain-joined machines are to receive the certificate, we can use the default “Domain Computers” group. That's probably not what you want though. You should create a AD Security Group specifically for this purpose (you can nest groups remember).
Also add “Enroll” if you want the ability to manually grab the certificate.
Within the certificate template, on the “General” tab ensure you have ticked “Publish certificate to Active Directory”.
Now we've prepared our certificate template, lets publish it for auto-enrollment!
Within the Certification Authority MMC snap-in, locate the Certificate Templates folder, right click and select New Certificate Template to Issue
Note that you may need to wait for AD Replication to occur if you have only just created your Certificate Template before it appears in this wizard. (You can force replication by logging onto an Active Directory Domain Services domain controller and running repadmin /syncall /force)
Follow the wizard and be sure to choose the template you have just created.
That's it!
Machines in the chosen security group will now automatically enroll for this certificate and receive a certificate from the issuing CA, which will be installed on the local machine.
Certificate enrollment will happen at the next group policy update. This happens automatically every ~90 minutes, or you can force with a gpupdate /force command on the machine in question.
You can check that the certificate has been issued by going on any given machine, opening certlm.msc and checking the personal store, or you can review the Issued Certificates within the Certificate Authority MMC snap-in on the issuing CA server.
Troubleshooting tips for ADCS certificate auto-enrollment
Firstly ensure that the AD replication has completed recently, and there's no other AD issues, with dcdiag command on a AD domain controller. Also you'll want to be sure that the machine has updated machine policy since you published the certificate template. Bouncing the machine in question will force a reapply, if you've had no luck with the gpupdate command above.
If your certificate does not automatically get issued, double check the Template permissions and members of the applicable security group.
Another reason as to why auto-enrollment isn't working – maybe that your template is an ADCS “V1” template rather than an ADCS “V2” or “V3” template - see this article from Microsoft on how to resolve this specific issue: https://learn.microsoft.com/en-us/archive/blogs/alextch/certificate-auto-enrollment-configuration-and-certificate-template-version
Written by Ryan Drake
Infrastructure Insider - Editor-in-Chief
Copyright 2023, All Rights Reserved.

